Hl2rp Serial Key Leak Forums
- Hl2rp Serial Key Leak Forums 2017
- Serial Key Generator
- Hl2rp Serial Key Leak Forums Free
- Serial Key Idm
Will I get a product key, can I get a product key?
Microsoft roadmap leaks for Office 15, IE 10 and more key products. Screen shots of a Microsoft product roadmap for partners have leaked to the Web.
- The key a well balanced face is to cleanse regularly with the right cleanser. At the request of the survivors the names have been changed. The layers should be thin and easy to remove, especially if you'll be moving indoors and outdoors often, such as when you're shopping at an outdoor mall.
- France: Paris. Home; Tarsus, Turkey; Chiang Mai, Thailand; Firenze, Italy; Freiburg Im Breisgau, Germany.
By default, Windows 10 builds are pre-keyed, meaning, you do not have to enter a product key and should not be prompted to enter one even after Windows 10 has completed setup.
Microsoft tells me that it will be possible to do so. And that a key part of this process is that it will save a product key tied to the previously upgraded PC or device in Windows Store. This is how Windows 10 will later know that the install is allowed: It’s “one of the benefits of the new delivery system,” a Microsoft representative told me.
Source: https://www.thurrott.com/windows/windows-10/3898/a-few-more-answers-about-windows-10-upgrades
Will ISO media be provided for the final release?
Yes, you will be able to download ISO media for Windows 10 RTM.
Please note, you might have to download the appropriate edition of Windows 10 for the version/edition of Windows you are upgrading. If you upgrade to the wrong edition, ie. Windows 7 Home Premium to Windows 10 Pro, you will have to purchase a license for Windows 10 Pro or go back to Windows 7 Home Premium and upgrade to Windows 10 Home.
Resources: How to: upgrade from previous versions of Windows using Windows 10 ISO file
Hl2rp Serial Key Leak Forums 2017
Suppose I need to reinstall Windows 10 after one or two years from now or I install a new hard disk?
Windows 10 is registered to the device, not your hard disk. Just install a new hard disk and reinstall Windows 10 and it will reactivate automatically.
Also:
• Create up to 4 virtual drives to mount many images.  Features: • Virtualization drives. • Advanced Mount is an important feature of DAEMON Tools Lite. It allows you to mount all kind of disc image files and copies up to 4 DT + SCSI + HDD devices.
Features: • Virtualization drives. • Advanced Mount is an important feature of DAEMON Tools Lite. It allows you to mount all kind of disc image files and copies up to 4 DT + SCSI + HDD devices.
This week may have been, perhaps, the closest thing the cybersecurity world can experience to a lull in the digital mayhem. With the exception of one very significant Apple leak—and we'll get to that—hackers kept their breaches, disruptions, and scams close to the baseline. At least, that we know of.
One of the most significant news stories of the week was, in fact, a massive law enforcement takedown. A joint operation of the Department of Homeland Security and cops in the US, Australia, and Europe arrested 13 people involved in the cybercrime forum Infraud, out of a total of 36 indicted individuals accused of more than half a billion dollars in fraud and hacking. The investigation led by Robert Mueller into Russian interference in the 2016 election and potential collusion with the Trump campaign has only picked up steam, despite the #releasethememo sideshow. A group of academic researchers released an AI tool that can automatically scan online privacy policies and then create readable visualizations of what a company or service does with your data.
Other news was more foreboding, if not quite the usual doom and gloom: Israeli researchers showed they could exfiltrate stolen data from a disconnected computer using the magnetic transmissions of its processor, even through Faraday shielding. We took a look ahead at the digital security of the 2018 election, which is protected by only a mishmash of inconsistent safeguards against hacking. Bitcoin fraudsters, meanwhile, adapted a well-worn scam to lure marks into sending them cryptocurrency.
And there's more. As always, we’ve rounded up all the news we didn’t break or cover in depth this week. Click on the headlines to read the full stories. And stay safe out there.
Apple's iBoot Leak Could Be a Major Boon to iPhone Hackers
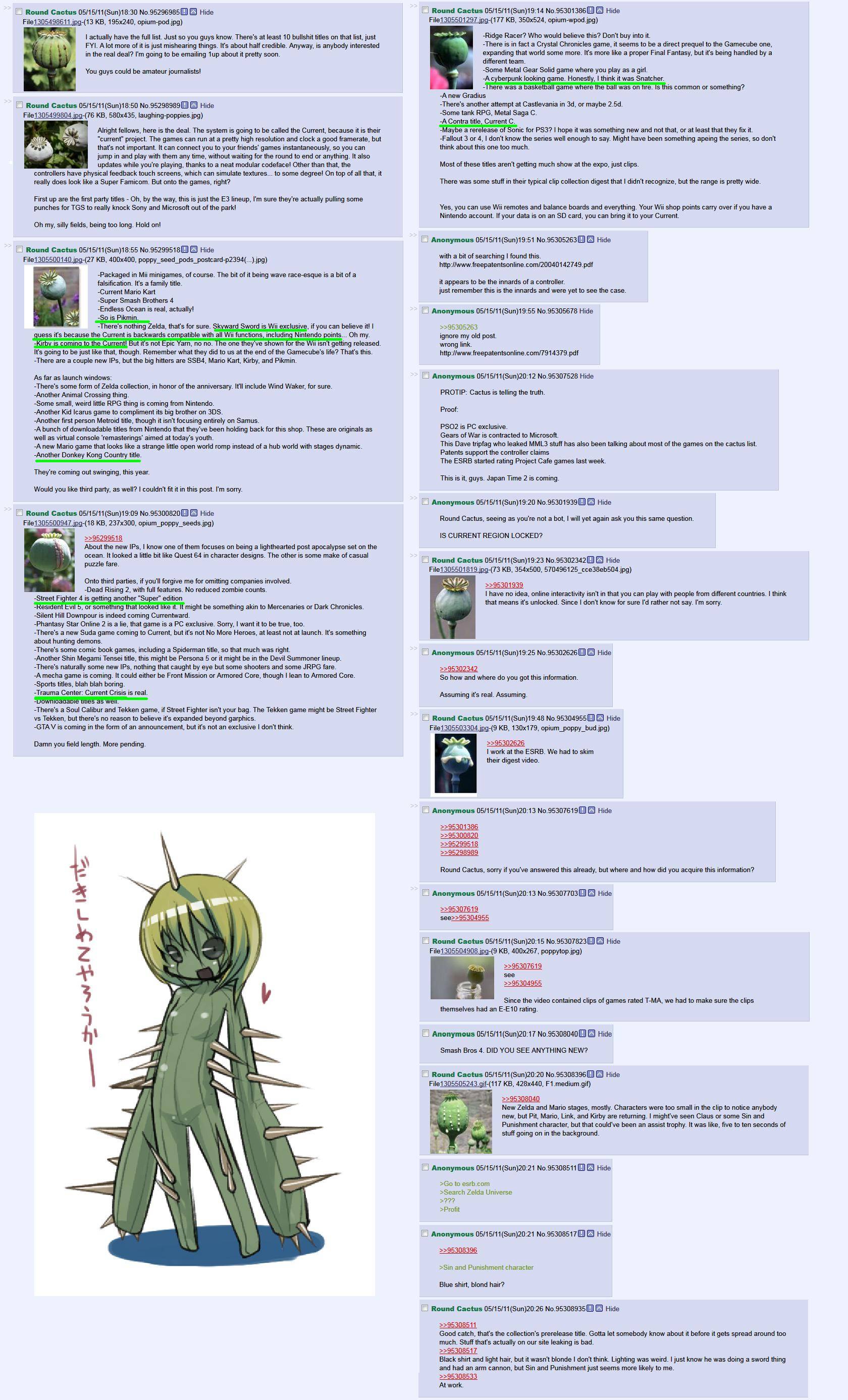
In most instances, Apple is pretty much the opposite of an open-source software company. So when the source code for a key component of iOS known as iBoot inexplicably leaked onto Github this week, it represented a significant revelation—and a serious security event. The leak, despite only exposing the iOS 9 version of iBoot rather than more modern versions, nonetheless offers iPhone hackers an opportunity to scour Apple's code for bugs like never before. The code had, according to several Apple-focused hackers, already circulated for months, meaning that sophisticated state-sponsored hackers likely already had access to it. But since appearing on Github, a much more public venue, the code became low-hanging fruit for a much broader group of hackers. Apple sent a copyright takedown notice to Github to remove the code—but in doing so, also confirmed that it was real. After first reporting the story of the leak, Motherboard followed up with a report that it had come from a low-level Apple employee who shared it with friends in the jailbreaking community.
Inside the Life of a Low-Level North Korean Hacker
North Korea's most elite and dangerous hackers, widely known by the codename Lazarus, have become notorious for their brazen and skilled penetrations of everything from SWIFT banking networks to Sony Pictures. But aside from that high-level force, North Korea also employs an army of rank-and-file criminal hackers, tasked with the drudgery of low-level cybercrime aimed at simply earning as much money as possible in the shortest amount of time. Bloomberg Businessweek tells the rare story of one of those hackers. Sent across the border China to live as an indentured hacker in a Kim regime facility, he spent his days finding flaws in gambling sites and writing gold-farming bots for online games. Life for these plebeian hackers, as the story describes it, is worse than unglamorous. One North Korean hacker in Beijing was severely beaten by his colleagues after accepting kimchi from a South Korean businessman. Another died of dengue fever, and his superior burned his body rather than send him back across the border to his home in North Korea.
Russian Operatives Offered to Sell US Stolen NSA Documents and Dirt On Trump
The New York Times has a pretty extraordinary tale of purported Russian operatives who offered to sell stolen NSA hacking tools—and dirt on President Donald Trump—back to the agency last fall. While the sale ultimately didn't go through, after US intelligence officials suspected something was amiss, the account is full of compelling details, and unique insight into modern-day international espionage. Including, just as a for instance, that the NSA used its official Twitter handle to send coded messages. The spirit of John Le Carré is alive and well on social media!
This Australian Startup You've Never Heard of Can Crack Your iPhone or Chrome Browser
Companies operating in the grey market for zero-day exploits—selling secret hacking techniques to government customers—have long had an abysmal reputation. That's mostly thanks to firms like NSO and Hacking Team, whose tools have ended up in the hands of authoritarian regimes that use them for surveillance of victims like journalists and activists. But Motherboard this week profiled a secretive startup called Azimuth Security, founded by well-known, highly respected hacker Mark Dowd, that represents another side of that shadowy industry. Sources describe Azimuth as both highly capable at developing exploits for hacking targets as hardened as iOS and Chrome, and also principled, offering those hacking tools only to governments in the US, Britain, Australia, New Zealand and Canada. Motherboard also offers an updated price list for modern exploits: Over $2 million for a no-interaction zero-day exploit for an iPhone, and a Chrome exploit that can escape the browser's sandbox to take over the rest of the computer can sell for $500,000 to $1 million.
Bug in Grammarly's Chrome Extension Exposed Personal Data
The grammar-checking tool Grammarly scrambled early this week to patch a flaw in its Chrome extension that exposed authentication tokens. This could have let websites access users' Grammarly account data, like documents, logs, and history. Tavis Ormandy, a researcher at Google's Project Zero, found the bug and notified Grammarly on February 2. The company released its patch to the extension's 22 million users through an automatic update on Monday. Ormandy characterized the vulnerability as 'high severity' and noted that it was relatively easy to exploit. A Grammarly spokesperson said there isn't evidence that the bug was actually targeted in the wild.
The Department of Justice charged two men on Monday with bank fraud related to a string of ATM attacks in which they allegedly stole thousands of dollars. 21-year-old Argenys Rodriguez from Massachusetts and 31-year-old Alex Alberto Fajin-Diaz, a Spanish national, were allegedly caught collecting $20 bills from an ATM using a 'jackpotting' attack, in which attackers use hardware and software tools to manipulate an ATM into spitting out cash. The men could face up to 30 years in prison.
The attack generally involves two phases—first attackers (often dressed as technicians) approach an ATM to hijack it, and then others return for the dangerous task of initiating the payout and collecting the money. Rodriguez and Fajin-Diaz were arrested on January 27, and police say they found jackpotting tools and more than $9,000 in $20 bills in their car. Some reports indicate that they may have collected more then $50,000 during a spree. At the end of January the Secret Service began issuing warnings about jackpotting attacks in numerous regions of the US that have already caused more than $1 million in losses. Jackpotting attacks have spread across Asia, Europe, and Central America over the last couple of years, but are new to the US.
Serial Key Generator
Related Video
SecurityHl2rp Serial Key Leak Forums Free
The iOS 11 Privacy and Security Settings You Should Set Up Right Now
Serial Key Idm
Heads up, iPhone owners. iOS 11 comes with a batch of security features that merit your attention.